Hello! I’m glad you enjoy the blog (and thank you for being the first asker!!). To tell you the truth, you can absolutely automate this but I do it all manually (so any tagging mistakes are due to me miss-typing or not noticing things). You’re correct about the public IP scanning, the easiest way to do this is using things like Shodan, Censys, and similar internet-of-things scanners, though you can also sort-of do it through Google using dorking/”Google Dorks”, which is a process of searching very specific text strings to find results which may not be accessible through a typical search query.
Previously I’d say Google Dorking was one of the easier/best ways to try it, but Google dislike people using their search engine in ways that aren’t intended so you might come up against some roadblocks (eg. Google throwing up a captcha and telling you they’ve “noticed some suspicious traffic from your IP address” - this is because dorking can sometimes look like bot or crawler activity, and they don’t like people doing that).
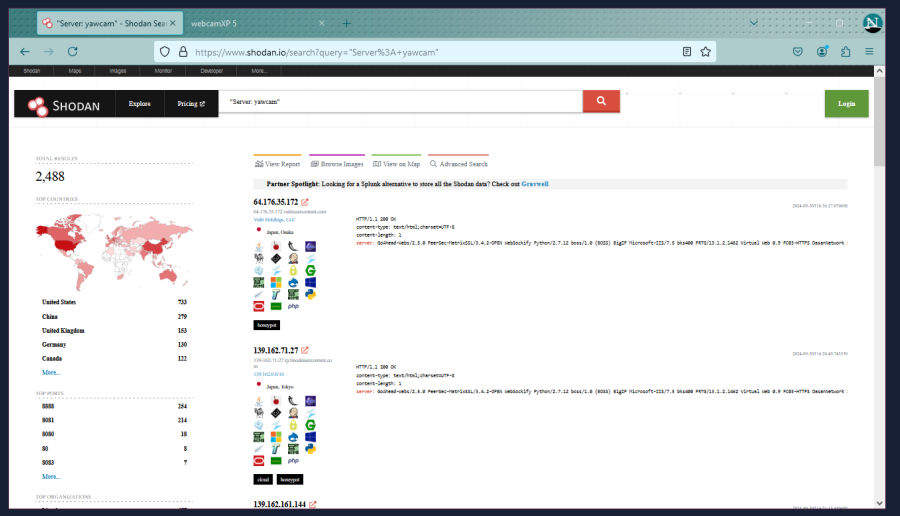
I’d say the best tool to use is Shodan. They do have a search query limit and only allow you to see the first two pages on results (full disclosure/bias disclosure, I have a membership (and got it on sale many years ago) and Shodan is generally my preference because it’s what I’ve been using the longest), but their search syntax is very easy to use and they have a lot of information. Also, if you’re interested in automating parts of this, Shodan (and similar services) have tools and an API that can help with this.
To explain how I do it, I’ll use an example with Google and then an example with Shodan.
Also before getting to the how-to, I just want to stress a couple of things;
(I’m also going to mirror this on Neocities here because I’ve been meaning to start making guides for ages and this is a good place to start)
With end-goal of dorking, for what we’re trying to do, is going to be to try to find the web-accessible page for a camera/s. There are a lot of lists online which will give you a bunch of jumping off points, but after you’ve been doing this a while it gets very easy to work out new ones.
Starting with something easy, we’ll try searching for cameras hosted using WebcamXP 5; for this, we’ll search for intitle:"webcamXP 5” - to break this down, it’s looking specifically for pages which contain “webcamXP 5” in the title of the webpage.
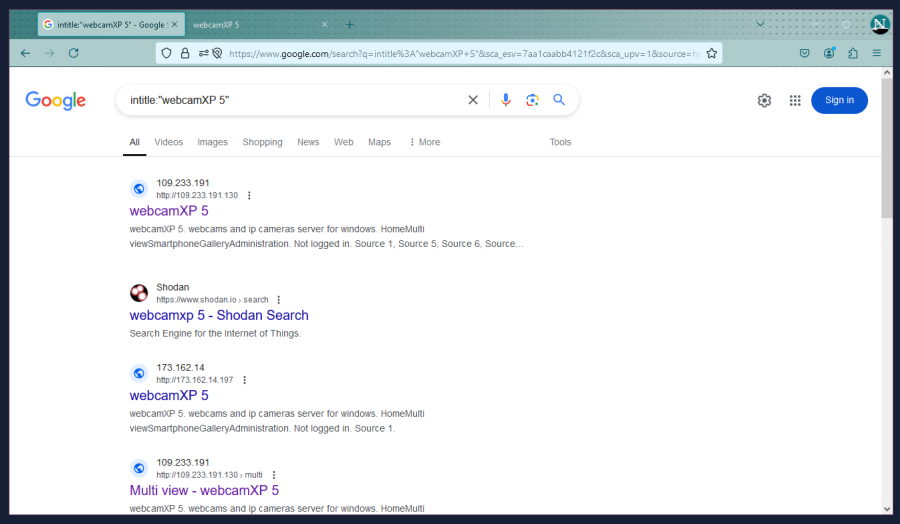
Result #1 and #3 here are what we’re looking for; they’re both IP addresses, whereas #2 is a regular website. Result #4 is just a different page on the same IP as #1.
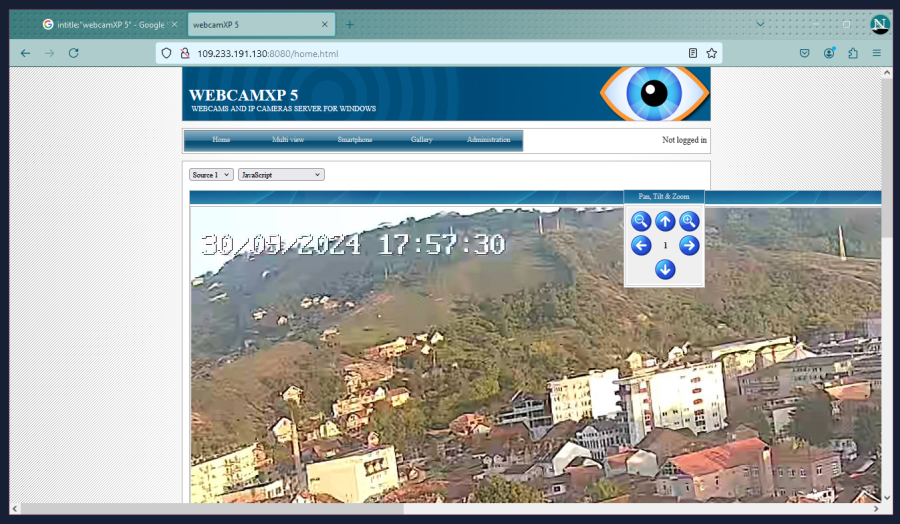
Clicking on result #1, we get taken to a WebcamXP 5 viewing page for a set of traffic observation cameras. You see these sorts of cameras run by radio stations and similar. Clicking on the [Source 1] drop down will display a number of other cameras hosted on the same IP, and you can view them one at a time; whereas “Multi View” in the top bar will allow you to view all cameras on the IP at once.
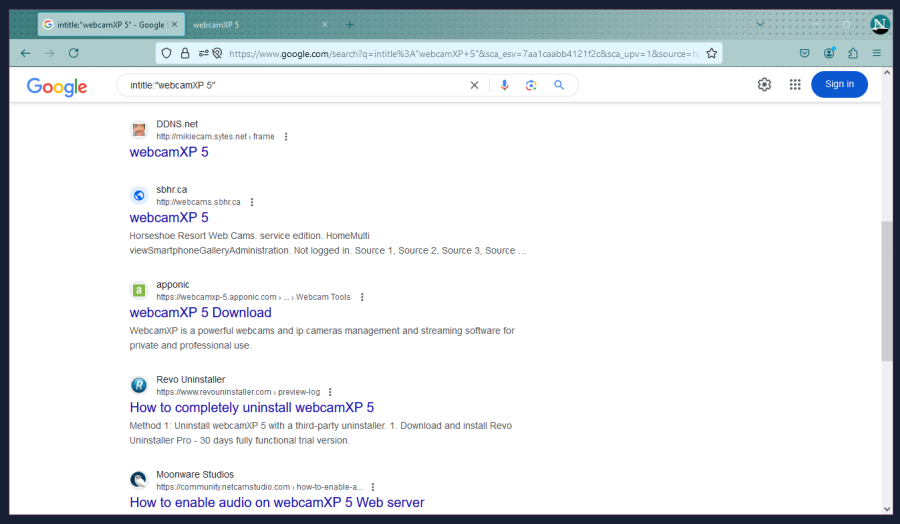
Here we can see some pages which aren’t IP addresses. Both result #1 and #2 shown here do link to actual cameras, but exercise caution when opening results even from Google. I’ve come across result #1 many times, so I know what it is, but it honestly looks pretty dodgy because:
Other things to look out for are if the title seems off. Where we have two pretty standard “webcamXP 5”, but you occasionally see ones that are just… slightly off and obviously trying to trick people.
Another thing is to look at the url preview just above the page title. Result #1 has the base URL then “>frame”, which I’ve seen many times with other legitimate webcamXP pages, but result #3 for example has “>Webcam Tools” which I haven’t, so if this were pretending to be a legitimate webcamXP 5 page, I’d be sceptical of.
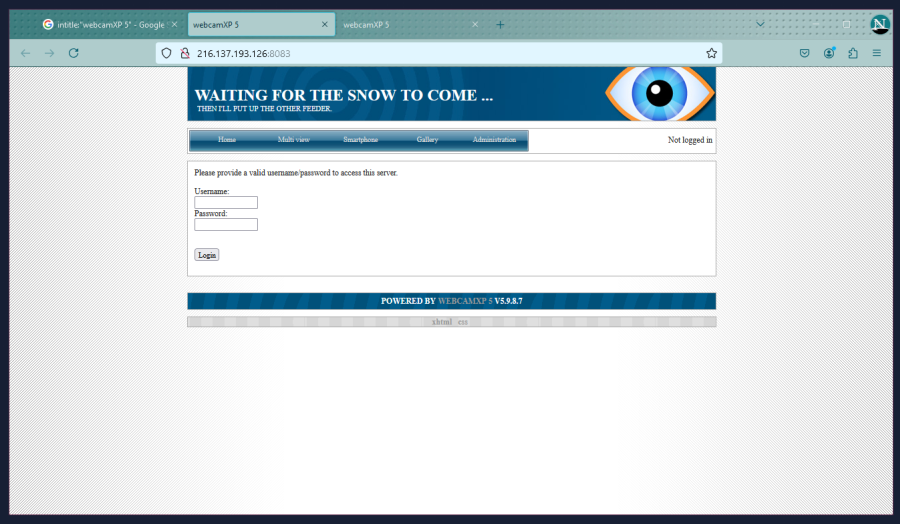
This is what the login page looks like. If you try to access a private camera, this is what will come up.

This is what will happen if Google thinks you’re a bot.
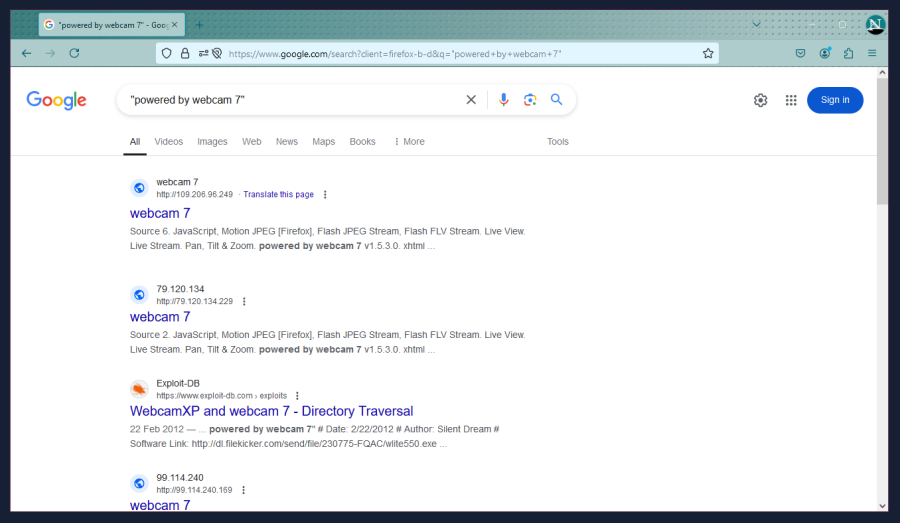
This is a lot more akin to a regular Google search, but still comes under dorking. This time we’re looking for cameras under webcam 7, which is a more recent version of WebcamXP 5
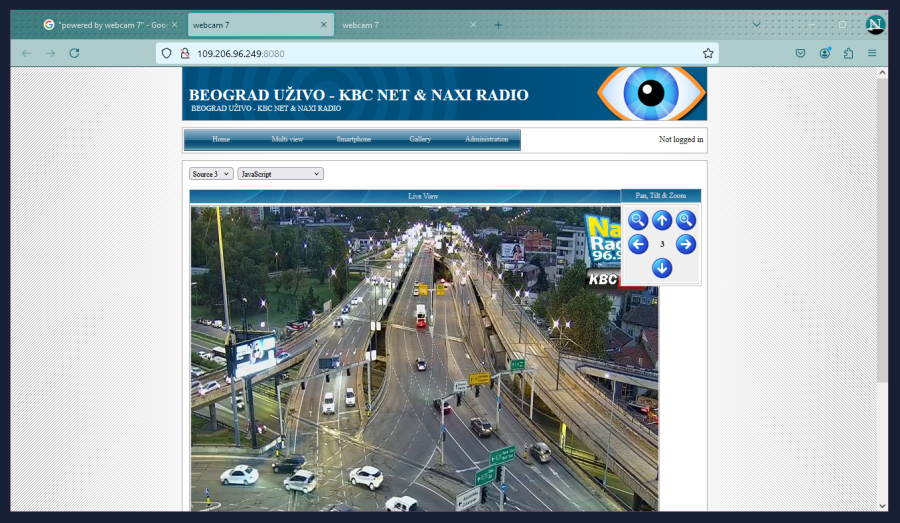
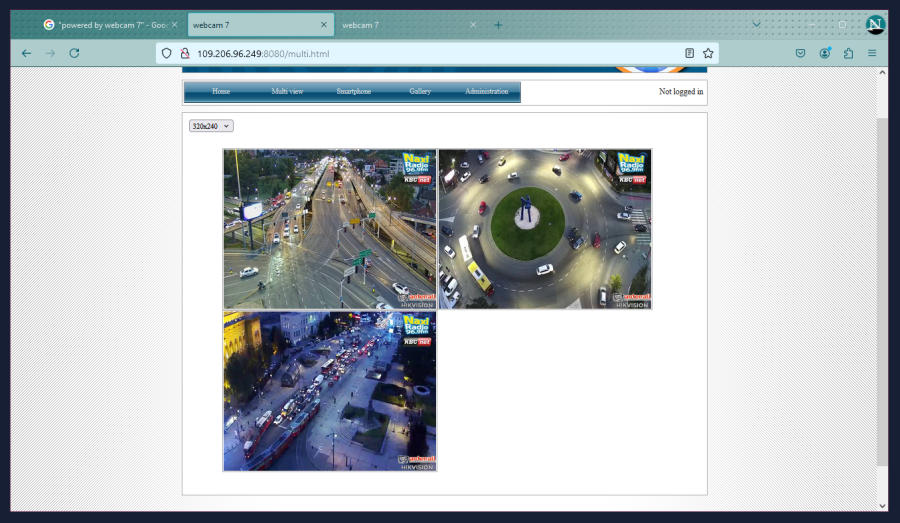
Main page and the “multi” camera page, this is a traffic webcam operated by a radio company.

Another example of one that’s meant to be publicly accessible. The camera feeds are likely present on the website mention, but this is a sort of… “backend portal” in a way (I know it’s not the actual meaning of backend in networking but you know)
From here it heavily depends on the camera type. For example, with these ones, you can literally just Right Click > Save As to get a JPEG still of the camera. For other camera brands and portals, there might be a dedicated screenshot button (eg. AXIS cameras often have a button to screenshot, but won’t allow you to Right Click > Save As straight from the feed).
For Shodan, let’s look for the same type of camera as before for easy comparison. There’s a few ways of doing this but my go-to way is for WebcamXP for example would be;
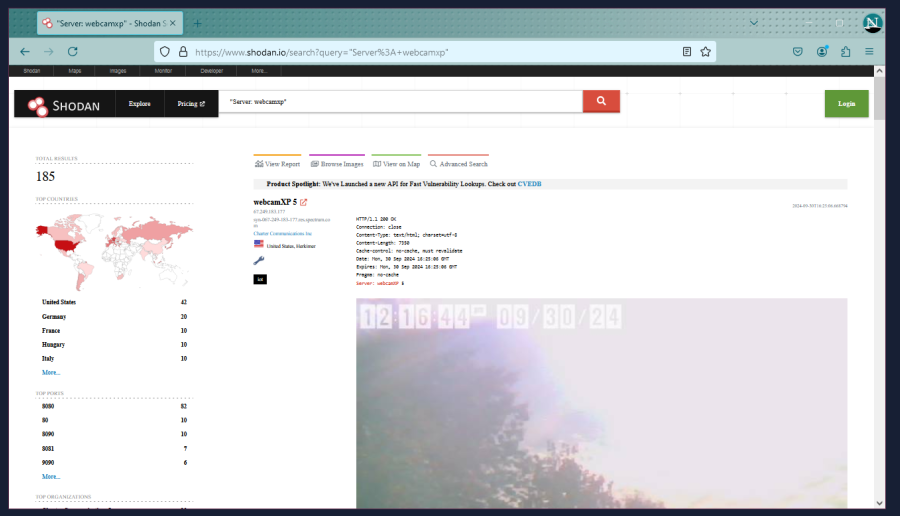
With Shodan, you get a bit more information, such as approximate location and for some… a screenshot! Very useful. Be aware that:
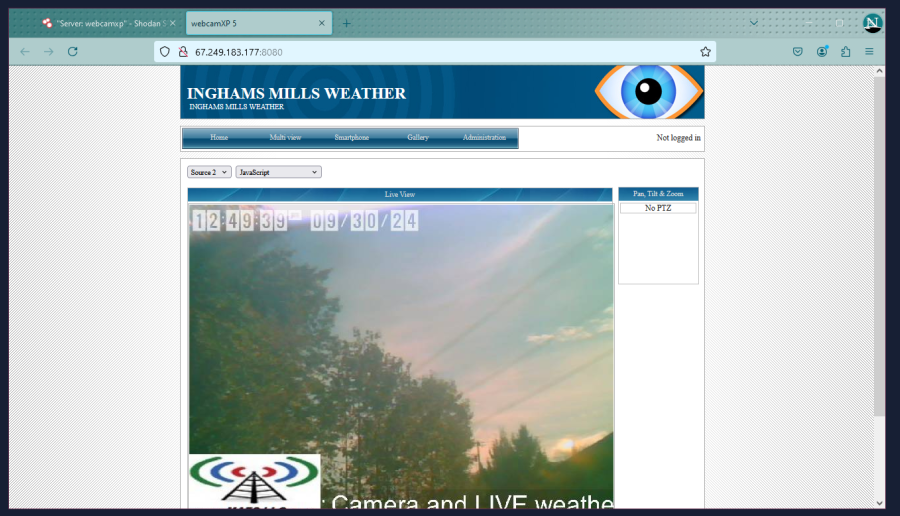
To open it, either copy and paste the IP address and correct port number, or click the little red icon next to the IP address to open it in a new tab.
An example of what a result that is a honeypot might look like; including tag.
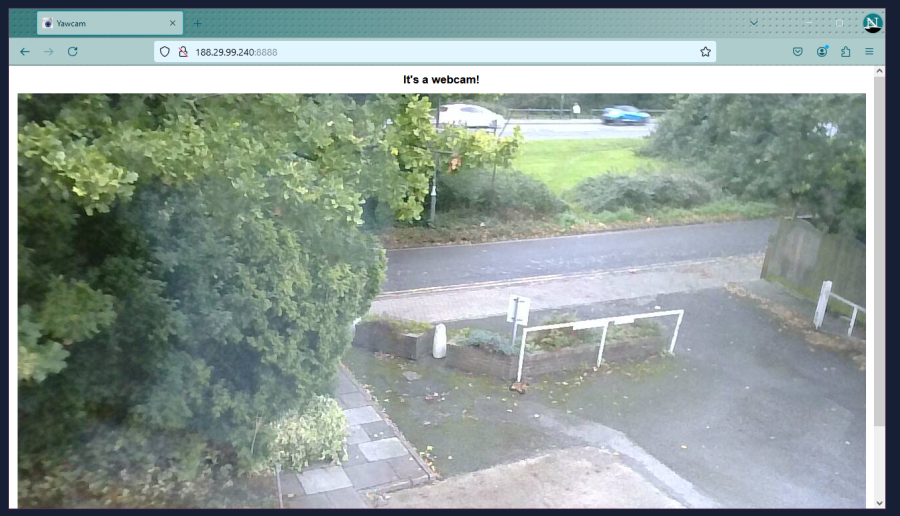
Example of an IP camera running Yawcam to display.